By khoanc, at: 18:30 Ngày 04 tháng 6 năm 2023
Thời gian đọc ước tính: __READING_TIME__ phút
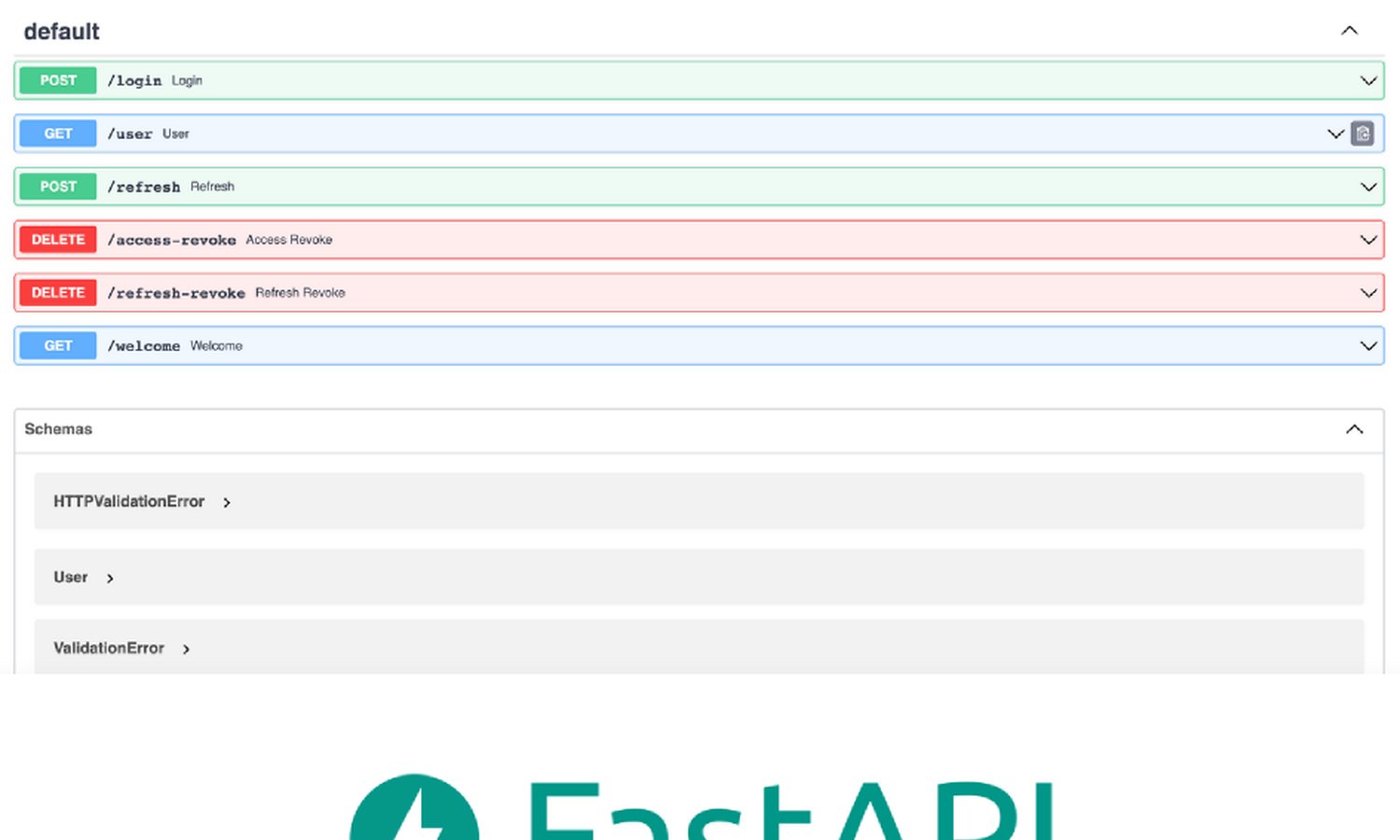
By khoanc, at: 18:30 Ngày 04 tháng 6 năm 2023
Thời gian đọc ước tính: __READING_TIME__ phút


Tháng 5 04, 2023
Đọc thêm